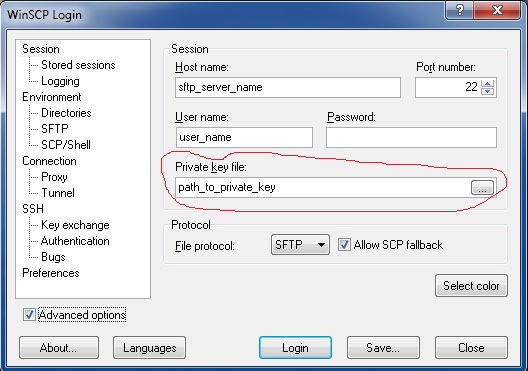
OpenSSH Server key management for Windows using the Windows tools or PowerShell. Drama club8th grade ela page.
In OpenSSH, host keys are usually stored in the /etc/ssh directory, in files starting with sshhostkey (the location can be changed in server configuration files). Host keys are normally generated automatically when OpenSSH is. Om nama sivaya mantra tamil downloadyalasopa. Secure Shell or SSH is a network protocol that allows data exchange through a secure channel between two network devices. Primarily used on Linux and Unix based systems to access shell accounts, SSH was designed as a replacement for Telnet and other insecure remote shells, which send information, notably passwords, in plaintext that make it easy to be caught up.
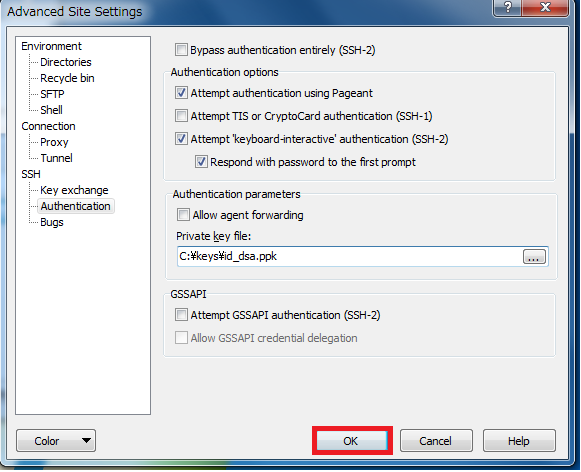
Winscp Ssh Private Key Passphrase
The memorized host keys are called known host keys and they are stored in a file called knownhosts in OpenSSH. As long as host keys don't change, this appoach is very easy to use and provides fairly good security. February . However, in large organization and when the keys change, maintaining known hosts files can become very time-consuming. WinSCP Download - how to import an OpenSSH formatted Private and Public Key Pair into WinSCP for use with SSH and SFTP.
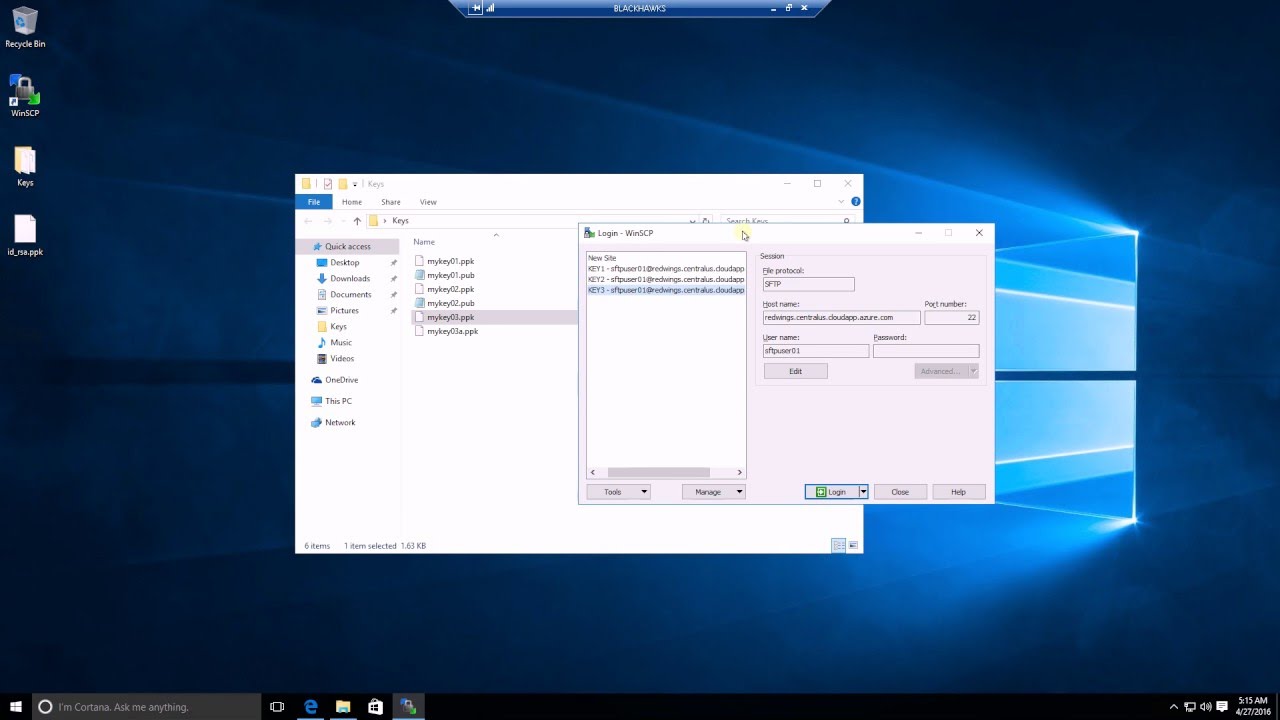
Winscp Key Pair
While OpenSSH 6.9 supports these by default:
Which means that the following are common:
However, WinSCP is still using the old SSH2_MSG_KEX_DH_GEX_REQUEST_OLD message. Support for the old deprecated message was removed in OpenSSH 6.9:
Which means that WinSCP cannot successfully negotiate diffie-hellman-group-exchange-* ciphers. For this reason, they were blacklisted for WinSCP clients in OpenSSH 6.9:
This leaves WinSCP with diffie-hellman-group14-sha1. SHA-1 is deprecated and insecure, and security-conscious SSH server administrators disable SHA-1 key exchange mechanisms. WinSCP can no longer negotiate any key exchange mechanism with OpenSSH 6.9 that is considered secure.
PuTTY 0.65 supports the newer message type. Additionally, PuTTY snapshots support newer protocols like curve25519 kex and the chacha20 cipher, which are a really good idea. WinSCP should update to at least 0.65, and the WinSCP team should notify the OpenSSH developers of the minimum version number that will support the new message type, so they can limit the blacklist to older versions.